Here’s how I setup Remote access to Plex to using Tailscale MagicDNS [1] and HTTPS [2] with the official PMS Docker container [3].
Tailscale Configuration
Setup Tailscale MagicDNS and HTTPS by following Tailscale guides to create certificates and choosing a Tailscale hostname name. This example uses plex.tailnet-0000.ts.net as the Tailscale hostname.
Tailscale certs are stored in /var/lib/tailscale/certs and are generated from Let’s Encrypt, Plex cannot use these directly and they must be converted to a pkcs12 type certificate.
Create a pkcs12 type certificate and password with openssl
sudo openssl pkcs12 -export -passout pass:"set_your_pass_here" \
-out /var/lib/tailscale/certs/plex.tailnet-0000.ts.net.p12 \
-in /var/lib/tailscale/certs/plex.tailnet-0000.ts.net.p12.crt \
-inkey /var/lib/tailscale/certs/plex.tailnet-0000.ts.net.p12.key \
-certfile /var/lib/tailscale/certs/acme-account.key.pem
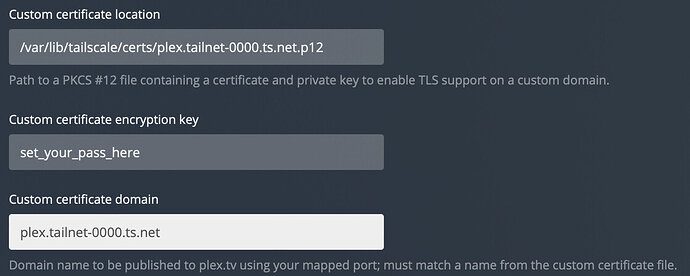
Then update the Plex->Network configuration with,
- Custom certificate location:
/var/lib/tailscale/certs/plex.tailnet-0000.ts.net.p12 - Custom certificate encryption key:
set_your_pass_here - Custom certificate domain:
plex.tailnet-0000.ts.net - Custom server access URLs:
https://plex.tailnet-0000.ts.net:32400
You can also include the Tailscale CIDR of 100.0.0.0/8 to LAN Networks and List of IP addresses and networks that are allowed without auth if desired.
If desired, make all traffic goes through Tailscale and local connections only by disabling Remote Access and Enable Relay.
Using Docker
If using the official Plex Docker container, mount the certificate as a volume and update ADVERTISE_IP and ALLOWED_NETWORKS, otherwise any changes made in the Plex UI or Preference.xml will be overwritten when the container restarts,
volumes:
- /var/lib/tailscale/certs/plex.tailnet-0000.ts.net.p12:/var/lib/tailscale/certs/plex.tailnet-0000.ts.net.p12:ro
- ADVERTISE_IP=https://plex.tailnet-0000.ts.net:32400
- ALLOWED_NETWORKS=192.168.1.0/24,100.0.0.0/8
Automatic Certificate Renewal
According to the Tailscale documentation certificates are automatically renewed within the 90 day period [4]
Either methods renew certificates as needed, before their 90 day expiry. A certificate is automatically requested for renewal within the weeks before its expiry, when a certificate is fetched.
However this may or may not be the case according to this Github issue [5].
- Enabling HTTPS · Tailscale Docs
- FR: Add command hook to `tailscale cert` · Issue #5011 · tailscale/tailscale · GitHub
A hack around this to to re-run the tailscale cert command, re-generate the pkcs12 cert and restarting Plex in a cronjob. This could lead to a period where an expired cert is in-use, but should be good enough until a way to manually renew is added to Tailscale.
Here’s an example renew/restart script for a daily cronjob,
#!/bin/bash
#Vars
CERTDIR="/var/lib/tailscale/certs"
DOMAIN="plex.tailnet-0000.ts.net"
PASS="set_your_pass_here"
#Renew tailscale certs (this may or may not work
#see https://github.com/tailscale/tailscale/issues/5011)
tailscale cert \
--cert-file=${CERTDIR}/${DOMAIN}.crt \
--key-file=${CERTDIR}/${DOMAIN}.key \
${DOMAIN}
#Create pkcs12 certificate from tailscale certs with a password
openssl pkcs12 -export -passout pass:"${PASS}" \
-out ${CERTDIR}/${DOMAIN}.p12 \
-in ${CERTDIR}/${DOMAIN}.crt \
-inkey ${CERTDIR}/${DOMAIN}.key \
-certfile ${CERTDIR}/acme-account.key.pem
#Set proper permissions on pcks12 cert
chmod 644 ${CERTDIR}/${DOMAIN}.p12
#Restart plex container to pick up new cert
cd /git/pms-docker
docker-compose down && docker-compose pull && docker-compose up -d
Notes
Hostname Matching
The Tailscale hostname set in Custom certificate domain must match the hostname set in Custom server access URLs and in /var/lib/tailscale/certs/plex.tailnet-0000.ts.net.p12.
Verify the hostname in /var/lib/tailscale/certs/plex.tailnet-0000.ts.net.p12 with openssl,
openssl pkcs12 -in /var/lib/tailscale/certs/plex.tailnet-0000.ts.net.p12 \
-nodes -passin pass:"set_your_pass_here" | openssl x509 -noout -subject
File Permissions
The permissions of /var/lib/tailscale/certs/plex.tailnet-0000.ts.net.p12 must be set to 644 otherwise Plex may not have read access and not load the customer certificate, falling back to the default direct.plex one and giving a Certificate Mismatch error.
Plexamp and Tailscale
If using Plexamp, after setting up Tailscale hostname and verifying it’s working, disconnect Plexamp from the Plex account and re-connect in order for it to pick up the newly added Custom server access URLs.