Server Version#: 4.121.1
Player Version#: 4.121.1
OS: Ubuntu 22.04
Hardware: Intel 14 core 64GB RAM 10 x 2TB SSD R5
Network: 2 x 10Gb LACP
UFW : Disabled for now
Apparmor: disabled for now
New: New server and two new 10Gb Brocade ICX switches
First posting to this forum so.. Greetings… And I hate to dog pile on a topic seeming to be beaten like a dead duck… but… … not seeing trees for forest here: Goal is to document workflow to root cause for a bit more advanced / complex system.
I use to run plex on raspberry PI 4 with small nas appliance with 1Gb software nic but it was too much for it to run current movies, and NIC transfers was creating problems. I had a two more VMs also as front ends and they were ok… but I wanted to remove LAN transfer latency, as well as handle higher resolution movies. So I built a new one .. it plays local but has a lot of 20second play then studder, and remote .. again same experience. So I am assuming this is because its using gateway service to play and that is creating issue
But after a few weeks, still not able to get remote access to work.
Packet flow:
ISP/WAN IP → IP on WAN of PFsense interface → NAT rule 32403 TCP to 32400 to 172.16.100.110 + FW rule 32400 from * to * allow to 172.16.100.110 → 1Gb LAN → 10Gb Switch supporting Jumbo frames → 2 x 10Gb LAG → 10Gb NIC in host + VLAN tagged interface + bridge for KVM etc + IP of host 172.16.100.110
I know that is a more complex setup than your average bear.. but… that is what I need for that server to also host my other environments of systems.
Test Cycle:
Shell on Server
cd /var/lib/plexmediaserver/Library/Application Support/Plex Media Server/Logs
mv *.log /tmp/
systemctl restart plexmediaserver.service
systemctl status plexmediaserver.service
< active (running) since Fri 2023-12-29 08:30:04 EST; 7s ago>
netstat -an | grep 32400
tcp 0 0 0.0.0.0:32400 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:32400 127.0.0.1:50390 TIME_WAIT
tcp 0 0 127.0.0.1:50368 127.0.0.1:32400 TIME_WAIT
tcp 0 0 127.0.0.1:32400 127.0.0.1:50332 TIME_WAIT
tcp 0 0 172.16.100.110:32400 172.16.100.32:20419 FIN_WAIT2
tcp 0 0 127.0.0.1:32400 127.0.0.1:50360 TIME_WAIT
tcp 0 0 172.16.100.110:32400 172.16.100.158:40986 ESTABLISHED
tcp 0 0 172.16.100.110:53374 108.234.144.117:32400 ESTABLISHED
tcp 0 0 127.0.0.1:50374 127.0.0.1:32400 TIME_WAIT
tcp 0 0 172.16.100.110:53364 108.234.144.117:32400 TIME_WAIT
tcp 1 5076 172.16.100.110:32400 172.127.119.208:62345 CLOSING
tcp 0 0 127.0.0.1:32400 127.0.0.1:50342 TIME_WAIT
tcp 0 0 172.16.100.110:32400 172.16.100.32:52867 TIME_WAIT
tcp 0 0 127.0.0.1:32400 127.0.0.1:50302 TIME_WAIT
tcp 0 0 127.0.0.1:32400 127.0.0.1:50358 TIME_WAIT
tcp 0 0 172.16.100.110:32400 172.16.100.32:20455 FIN_WAIT2
tcp 0 0 172.16.100.110:32400 172.16.100.32:20422 FIN_WAIT2
tcp 0 0 172.16.100.110:32400 172.16.100.32:20446 ESTABLISHED
tcp 0 0 127.0.0.1:32400 127.0.0.1:50326 TIME_WAIT
tcp 0 0 127.0.0.1:32400 127.0.0.1:50362 TIME_WAIT
tcp 0 0 127.0.0.1:32400 127.0.0.1:50316 TIME_WAIT
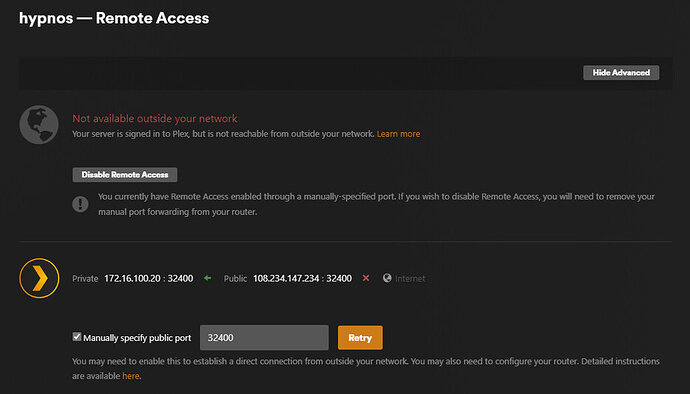
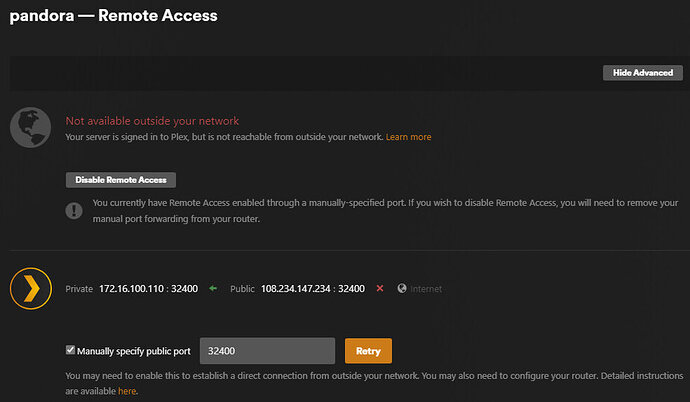
GUI in plex
Settings → Remote Access → Manual port 32403 → Retry → flips green for 2 seconds then back to fail.
< collect logs in GUI >
Log Review
Not sure in forum how to attached to thread as zip but cut out what I think is relevlant:
“Plex Media Server.log” seems to be the relevant log for this issue and search for “32403”
7944726328] DEBUG - Completed: [172.16.100.32:20509] 200 GET /myplex/account (6 live) #b7 TLS GZIP 2770ms 4051 bytes (pipelined: 55)
Dec 29, 2023 08:31:55.692 [139697839762232] DEBUG - Request: [172.16.100.32:20509 (Subnet)] GET /myplex/account (6 live) #b8 TLS GZIP Signed-in Token (LordVisigoth) (Microsoft Edge)
Dec 29, 2023 08:31:55.694 [139697944726328] DEBUG - Completed: [172.16.100.32:20509] 200 GET /myplex/account (6 live) #b8 TLS GZIP 1ms 4053 bytes (pipelined: 56)
Dec 29, 2023 08:31:55.694 [139697907448632] DEBUG - [Req#6d] MyPlex: Sending Server Info to myPlex (user=nobody@gmail.com, ip=108.234.x.x, port=32403)
Dec 29, 2023 08:31:55.695 [139697907448632] DEBUG - [Req#6d/HCl#5c] HTTP requesting POST https://plex.tv/servers.xml?auth_token=xxxxxxxxxxxxxxxxxxxx
Dec 29, 2023 08:31:55.920 [139697839762232] DEBUG - Request: [172.16.100.32:20509 (Subnet)] GET /myplex/account (6 live) #ba TLS GZIP Signed-in Token (LordVisigoth) (Microsoft Edge)
Dec 29, 2023 08:31:55.922 [139697946835768] DEBUG - Completed: [172.16.100.32:20509] 200 GET /myplex/account (6 live) #ba TLS GZIP 1ms 4053 bytes (pipelined: 57)
Dec 29, 2023 08:31:56.187 [139697916107576] DEBUG - [HttpClient/HCl#5c] HTTP/2.0 (0.5s) 201 response from POST https://plex.tv/servers.xml?auth_token=xxxxxxxxxxxxxxxxxxxx
Dec 29, 2023 08:31:56.187 [139697907448632] DEBUG - [Req#6d] MyPlex: Published Mapping State response was 201
Dec 29, 2023 08:31:56.187 [139697907448632] DEBUG - [Req#6d] MyPlex: Got response for 1538de5a43d1b68f1ed0498e9f12c1ec1a0f223a ~ registered 108.234..x.x:32403
Dec 29, 2023 08:31:56.187 [139697907448632] DEBUG - [Req#6d] MyPlex: updating mapped state - current state: 'Mapped - Not Published'
Dec 29, 2023 08:31:56.187 [139697907448632] DEBUG - [Req#6d] MyPlex: mapping state set to 'Mapped - Publishing'.
Dec 29, 2023 08:31:56.187 [139697907448632] DEBUG - [Req#6d] MyPlex: async reachability check - current mapped state: 'Mapped - Publishing'.
Dec 29, 2023 08:31:56.187 [139697907448632] DEBUG - [Req#6d] MyPlex: Requesting reachability check.
Dec 29, 2023 08:31:56.187 [139697907448632] DEBUG - [Req#6d/HCl#5d] HTTP requesting PUT https://plex.tv/api/servers/1538de5a43d1b68f1ed0498e9f12c1ec1a0f223a/connectivity?X-Plex-Token=xxxxxxxxxxxxxxxxxxxx&asyncIdentifier=e330a39b-00c9-4b0f-a03e-5efdfacbef8c
Dec 29, 2023 08:31:56.326 [139697916107576] DEBUG - [HttpClient/HCl#5d] HTTP/2.0 (0.1s) 200 response from PUT https://plex.tv/api/servers/1538de5a43d1b68f1ed0498e9f12c1ec1a0f223a/connectivity?X-Plex-Token=xxxxxxxxxxxxxxxxxxxx&asyncIdentifier=e330a39b-00c9-4b0f-a03e-5efdfacbef8c (reused)
Dec 29, 2023 08:31:56.327 [139697907448632] DEBUG - [Req#6d] MyPlex: Updating device connections (from timer: 0)
Dec 29, 2023 08:31:56.327 [139697907448632] DEBUG - [Req#6d/HCl#5e] HTTP requesting PUT https://plex.tv/devices/1538de5a43d1b68f1ed0498e9f12c1ec1a0f223a?Connection[][uri]=http://108.234..x.x:32403&Connection[][uri]=http://172.16.100.110:32400&httpsEnabled=1&httpsRequired=0&dnsRebindingProtection=0&natLoopbackSupported=0&X-Plex-Token=xxxxxxxxxxxxxxxxxxxx
Dec 29, 2023 08:31:56.420 [139697839762232] DEBUG - Request: [172.16.100.32:20509 (Subnet)] GET /myplex/account (6 live) #bc TLS GZIP Signed-in Token (LordVisigoth) (Microsoft Edge)
Dec 29, 2023 08:31:56.421 [139697946835768] DEBUG - Completed: [172.16.100.32:20509] 200 GET /myplex/account (6 live) #bc TLS GZIP 1ms 4109 bytes (pipelined: 58)
Dec 29, 2023 08:31:56.474 [139697916107576] DEBUG - [HttpClient/HCl#5e] HTTP/2.0 (0.1s) 200 response from PUT https://plex.tv/devices/1538de5a43d1b68f1ed0498e9f12c1ec1a0f223a?Connection[][uri]=http://108.234..x.x:32403&Connection[][uri]=http://172.16.100.110:32400&httpsEnabled=1&httpsRequired=0&dnsRebindingProtection=0&natLoopbackSupported=0&X-Plex-Token=xxxxxxxxxxxxxxxxxxxx (reused)
Dec 29, 2023 08:31:59.455 [139697854626616] DEBUG - [NSB/SSDP] Parsing SSDP schema for http://172.16.100.7:9080
Dec 29, 2023 08:31:59.466 [139697916107576] DEBUG - [HttpClient/HCl#5f] HTTP/1.1 (0.0s) 200 response from GET http://172.16.100.7:9080 (reused)
Dec 29, 2023 08:32:01.451 [139697946835768] DEBUG - [EventSourceClient/pubsub/45.56.115.195:443] EventSource: Got event [data] '<Message address="108.234..x.x" port="32403" asyncIdentifier="e330a39b-00c9-4b0f-a03e-5efdfacbef8c" connectivity="0" command="notifyConnectivity"/>'
Dec 29, 2023 08:32:01.451 [139697946835768] DEBUG - [EventSourceClient/pubsub/45.56.115.195:443] PubSub: Got notified of reachability for async identifier e330a39b-00c9-4b0f-a03e-5efdfacbef8c: 0 for 108.234..x.x:32403 (responded in 5125 ms)
Dec 29, 2023 08:32:01.451 [139697946835768] DEBUG - [EventSourceClient/pubsub/45.56.115.195:443] MyPlex: reachability check - current mapping state: 'Mapped - Publishing'.
Dec 29, 2023 08:32:01.451 [139697946835768] DEBUG - [EventSourceClient/pubsub/45.56.115.195:443] MyPlex: mapping state set to 'Mapped - Not Published (Not Reachable)'.
Dec 29, 2023 08:32:01.458 [139697839762232] DEBUG - Request: [172.16.100.32:20509 (Subnet)] GET /myplex/account (5 live) #c1 TLS GZIP Signed-in Token (LordVisigoth) (Microsoft Edge)
Dec 29, 2023 08:32:01.459 [139697946835768] DEBUG - Completed: [172.16.100.32:20509] 200 GET /myplex/account (5 live) #c1 TLS GZIP 1ms 4118 bytes (pipelined: 59)
A bit vague..
nmap of server on LAN scan of host
Scanning pandora.penguinpages.local (172.16.100.110) [1000 ports]
Discovered open port 22/tcp on 172.16.100.110
Discovered open port 111/tcp on 172.16.100.110
Discovered open port 5900/tcp on 172.16.100.110
Discovered open port 3389/tcp on 172.16.100.110
Discovered open port 139/tcp on 172.16.100.110
Discovered open port 445/tcp on 172.16.100.110
Discovered open port 9090/tcp on 172.16.100.110
Discovered open port 9091/tcp on 172.16.100.110
Discovered open port 5901/tcp on 172.16.100.110
Discovered open port 2049/tcp on 172.16.100.110
Discovered open port 6547/tcp on 172.16.100.110
Discovered open port 873/tcp on 172.16.100.110
Completed SYN Stealth Scan at 08:38, 0.09s elapsed (1000 total ports)
Above not what I expected… every port BUT 32400… ??
I went back to old plex pi host and reinstalled plex and re-activated it on 32402 It also has same symptom. But I did not think to “save it” in old working state so as to have solid baseline, so re-install and configure and forwarding rules put back.. But tried it to rule out 10Gb / LAG / VLAN interface + bridge etc.. So I can’t know, but I don’t think its that.
nmap on PI
Discovered open port 22/tcp on 172.16.100.20
Discovered open port 111/tcp on 172.16.100.20
Again, not what I expected.. port 32400 not showing.
If I go to URL :
http://server.local.ip.address:32400/clients
401 Unauthorized
But so does PI system.. so.. Not sure what “…Plex App doesn’t appear in the XML there…” means but my guess is not a 401.. an example response success would help ![]()
Question:
Is there a more technical debug workflow on host validate workflow.. This document is a good start… but could use a bit more technical test steps…